I'm tied up for a day or two so if you can't sleep...
Any port in a storm
One of the problems with IPv4 is the limited number of addresses available – a shade over 4 billion – and for this reason IPv6 was developed. In the meantime NAT/PAT was developed as a workaround. The problem is, it's expensive to move from IPv4 to IPv6 so it will happen more gradually and NAT/PAT will plug the gap for a while perhaps even spilling over into IPv6 as there are some useful security features in it.
Before NAT/PAT you would need a public IP address for every device you wanted to connect to the Internet while now you 'hide' behind a relatively small number of public addresses, or even one. In the case of home users usually one address suffices. It's all done with ports!
The box you connect to the Internet with runs NAT/PAT by default, it works like this...
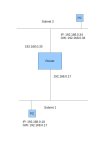
The ISP assigns the box all the relevant IP address information including public IP, subnet mask, default router and DNS (for name resolution)
Your PC gets a different IP address from the router, usually via DHCP and typically a 192.168.x.x network
Your PC tries to connect to a web server and figures out it's not on your network so sends the packet to the default router (the ISP box)
The default router has a NAT/PAT table of around 5000 entries typically and records where the request came from including IP address and port
It then sends the request to the web server on your behalf
The web server sees the request as originating from the router and sends the reply back
Your router looks up the original sender in the NAT/PAT table and forwards the reply back to you
Voila! You hide multiple devices behind fewer external IP addresses thus fooling the web server into thinking there's just one device.
The outcome is less strain on diminishing numbers of available IPv4 addresses and less need to worry about IPv6 for a while.
Mostly, home systems utilise PAT but if you add some NAT elements in you need to be aware of the risks.
When you initiate a connection to the Internet using PAT an entry is made into the state table to allow 'stateful inspection' of any replies received. Or, simply put, your router checks the sender is the system you connected to and not just some passing exploit.
Random external callers get blocked because there's no entry in the state table.
However, if you open a port you're telling the router to allow any traffic in on that port and redirect it to whatever IP address and port you specify. Stateful inspection is inactive for these connections and there may be security implications. Of course, if you want to allow the traffic in there's no choice.
When opening a port you may have to specify both TCP and UDP depending on the service type. A quick 'Google' will usually indicate which port(s) and protocols are used.
Binary and other painful things
Earlier I mentioned that sometimes the early technology pokes it's ugly head through our pleasant little GUI world.
In the early days of setting the classes routers were fairly brainless and slow so it was important to grab any efficiencies you could. Class A numbers go from 0. to 127. on the network side while Class B numbers go from 128. to 191. Why not just say 0 to 99, 100 to 199 etc. - it's easier!
The reason is that while we humans see the nice dotted-decimal notation of, say, 10.x.x.x the computer 'sees' 00001010.x.x.x and that means there's a zero in the most significant bit of the network octet – hold that thought!
If we look at a Class B network of, say, 163.x.x.x the computer 'sees' 10111111.x.x.x and now there's a 1 in the most significant bit.
Computer machine language has some fast instructions and some slow ones – speed is determined by how many clock 'ticks' elapse before you get the answer. The fewer the 'ticks' the quicker the result. Rotate Left (ROL) is very fast and simply moves the most significant bit into a flag that can be rapidly tested. Like this pseudo-code example...
Load first octet
Rotate Left
If flag=0 then class=A, do something
If flag=1 then class=B, do something different
Very fast!
For other classes additional Rotates quickly allow you to determine the class of the address range. This doesn't work very well with decimal range breaks as they're harder to test and much slower.
A curious rule of thumb
Because you don't want to be reading some tedious text while pursuing your networking goal just commit this to memory:
In many cases the first and last are unusable!
On this network, 192.168.0.0/24 (subnet mask 255.255.255.0) there are 256 addresses (0-255) but only 254 can be assigned. The reason is that the first (192.168.0.0) is the cable address and must not be assigned to a device while 192.168.0.255 is the broadcast address. The first address and last address of any subnet cannot be assigned to a device – they're unusable.
This crops up time and again.
Broadcasting yourself
All traffic is equal but some is more equal than others!
Some traffic is routable i.e. it can get off the network to another one, like the Internet. Some traffic is not routable but still plays an important part. For example, DHCP is a broadcast technology and not naturally routable.
Broadcasts go to all devices as the target address is set to the broadcast address. In our example above the broadcast address is 192.168.0.255 and all devices, on seeing this address, check the contents. Non-broadcasts are directed to a specific address so while all devices look at what gets sent, as soon as they see it's not addressed to them they drop it.
If you have a home network with your ISP router set to give out IP addresses using DHCP and you add a router internally with a second subnet you need to tweak stuff.
You can either use static addresses for the new subnet or configure the internal router to pass DHCP traffic – sometimes known as DHCP helper or relay.
A nice layer cake
I suppose we'll have to include the OSI 7-Layer Model, at least a bit! Mainly interesting because it specifies what should happen at different levels, or layers, from hardware through to application.
Turn it on it's head for now and just look at layers 1, 2 and 3. It's where you'll mostly come unstuck anyway – or in my terms, get this right and the packet comes out the wall, after that it's not my problem!
Layer 1
Physical. We're talking plugs and bits of wire, socket types, current flows and voltages. Some devices may live here such as repeaters (hubs), not too bright stuff, routing flies over its head.
Layer 2
Data Link. Knows about MAC addresses and logical links. Lower protocols like Ethernet and PPP live down here. Devices such as simple switches live here too.
Layer 3
Network. Knows about routing and IP addressing. Higher protocols such as TCP and UDP live here along with cleverer switches than can route.
The layers interact by wrapping or unwrapping the information – a bit like a series of envelopes. So PC1, sending to PC2 constructs an IP packet at Layer 3 and passes it to Layer 2 which encapsulates the packet in a frame (envelope) – typically Ethernet. This is passed to Layer 1 which does the signalling on the wire.
PC2 receives the signal and converts it back to a frame which it passes to Layer 2. Layer 2 unwraps the frame to reveal the payload – the original IP packet with your data inside – which it passes to Layer 3 and so on.
And that's the point really, if you change something in a layer – like change to a different network card – then you only need to change stuff on your system at the affected layer(s). You don't re-install Windows to accommodate the new hardware – you just install a driver to link into the layers above.
[All is cool, all interfaces within normal parameters...]