No apologies for starting at the beginning gurus - chapter one is supposed to encourage people to have a go, not totally freak them out 
In the beginning
Once upon a time there were many protocols but the advance of the Internet means they have largely fallen by the wayside and IP has become the protocol of choice. Designed to be scalable from the outset, IP is really a suite of protocols with TCP being one. Others include UDP and ICMP.
As the cost of communications technology has fallen, the Internet has spread and more people have multiple technology types in the home. The home network has become more complex than it ever was and a better understanding of how networking works may be useful.
This is a practical look at how stuff works rather than an academic exploration. When you're up to your wotsits in network cables and communications kit that doesn't work you won't be reaching for a well-thumbed copy of “The OSI 7-layer Model Explained”!
IP in perspective
IP networking was conceived decades ago, originally so the Pentagon could reliably bomb places like Russia. However, while it has been continually updated, some of the original remnants of the old technology rear their heads from time to time. It is useful to know about this as it explains some stuff that is otherwise incomprehensible.
When IP was developed, communications equipment was configured by specialists writing in machine code – the basic computer-speak – almost at binary level. Code had to be efficient so it would run quickly and some instructions run faster than others. Built into IP are apparent anomalies that are explained when you look at the binary. Such as what the subnet mask does, why you can't assign an IP address of 192.168.0.0 and why the so-called Classes have unusual number boundaries.
First though, a quick picture.
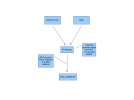
It's a flowchart for what happens when you try to connect to summat by name over an IP network. The name gets resolved to an IP address using either DNS (Dynamic Name Service) or by doing a lookup on the local HOSTS file. The IP address of the system you are trying to connect to will have been provided either by DHCP or manually (Static). You don't have to do the name resolution bit if you know the IP address already.
ARP (Address Resolution Protocol) is used to resolve the MAC address and, finally, something gets sent.
If you're sending to the Internet or anything on a different network (even if it's in your house) there's another stage – routing.
When a device attempts to send, it needs to know if the target is on the same network as itself or not. It does this by comparing its own IP address with the target's IP address and uses the subnet mask to get rid of uninteresting bits. That's what the subnet mask is for.
Same network example:
Sender IP 192.168.0.10
Target IP 192.168.0.20
Subnet mask 255.255.255.0
The subnet mask says ignore the last octet (8 bits, the IP address comprises 4 octets separated by dots). The 255 means check this, the 0 means forget it. A quick check shows that 192.168.0 is the network part and the same for both source and target so the packet gets sent direct.
Different network example:
Sender IP 192.168.0.10
Target IP 192.168.10.20
Subnet mask 255.255.255.0
Same subnet mask so we're only interested in the first three octets and this time 192.168.0 is clearly not equal to 192.168.10 – the target is on a different network. In this case send the packet to the default router.
We therefore need three key numbers to make our network do something, IP address, subnet mask and default router address. Actually, you only need the default router address if you want to connect to another network, like the Internet, but let's assume we will always want to do this. All that lot is IPv4, forget IPv6 for now as unless you're working in the IT industry you'll likely not need to worry about it for years.
[Hope it's useful - let me know before I post more ]
]
In the beginning
Once upon a time there were many protocols but the advance of the Internet means they have largely fallen by the wayside and IP has become the protocol of choice. Designed to be scalable from the outset, IP is really a suite of protocols with TCP being one. Others include UDP and ICMP.
As the cost of communications technology has fallen, the Internet has spread and more people have multiple technology types in the home. The home network has become more complex than it ever was and a better understanding of how networking works may be useful.
This is a practical look at how stuff works rather than an academic exploration. When you're up to your wotsits in network cables and communications kit that doesn't work you won't be reaching for a well-thumbed copy of “The OSI 7-layer Model Explained”!
IP in perspective
IP networking was conceived decades ago, originally so the Pentagon could reliably bomb places like Russia. However, while it has been continually updated, some of the original remnants of the old technology rear their heads from time to time. It is useful to know about this as it explains some stuff that is otherwise incomprehensible.
When IP was developed, communications equipment was configured by specialists writing in machine code – the basic computer-speak – almost at binary level. Code had to be efficient so it would run quickly and some instructions run faster than others. Built into IP are apparent anomalies that are explained when you look at the binary. Such as what the subnet mask does, why you can't assign an IP address of 192.168.0.0 and why the so-called Classes have unusual number boundaries.
First though, a quick picture.

It's a flowchart for what happens when you try to connect to summat by name over an IP network. The name gets resolved to an IP address using either DNS (Dynamic Name Service) or by doing a lookup on the local HOSTS file. The IP address of the system you are trying to connect to will have been provided either by DHCP or manually (Static). You don't have to do the name resolution bit if you know the IP address already.
ARP (Address Resolution Protocol) is used to resolve the MAC address and, finally, something gets sent.
If you're sending to the Internet or anything on a different network (even if it's in your house) there's another stage – routing.
When a device attempts to send, it needs to know if the target is on the same network as itself or not. It does this by comparing its own IP address with the target's IP address and uses the subnet mask to get rid of uninteresting bits. That's what the subnet mask is for.
Same network example:
Sender IP 192.168.0.10
Target IP 192.168.0.20
Subnet mask 255.255.255.0
The subnet mask says ignore the last octet (8 bits, the IP address comprises 4 octets separated by dots). The 255 means check this, the 0 means forget it. A quick check shows that 192.168.0 is the network part and the same for both source and target so the packet gets sent direct.
Different network example:
Sender IP 192.168.0.10
Target IP 192.168.10.20
Subnet mask 255.255.255.0
Same subnet mask so we're only interested in the first three octets and this time 192.168.0 is clearly not equal to 192.168.10 – the target is on a different network. In this case send the packet to the default router.
We therefore need three key numbers to make our network do something, IP address, subnet mask and default router address. Actually, you only need the default router address if you want to connect to another network, like the Internet, but let's assume we will always want to do this. All that lot is IPv4, forget IPv6 for now as unless you're working in the IT industry you'll likely not need to worry about it for years.
[Hope it's useful - let me know before I post more
