Twitter phishing hack hits BBC, PCC … and Guardian
An invitation to find out about better sex is spreading virally around Twitter – but only leads to identity theft and malware
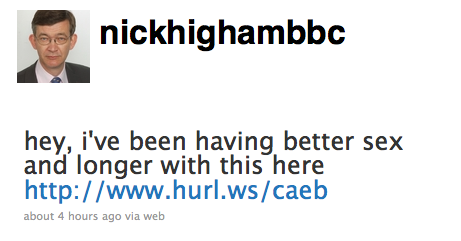
Nick Higham of the BBC didn't send this message. And DO NOT follow the link.
Thousands of Twitter users have seen their accounts hijacked after a viral phishing attack which sends out messages saying "this you??" or "hey, i've been having better sex and longer with this here" and other sex-related "direct" messages.
Among those who fell victim were the Press Complaints Commission and the BBC correspondent Nick Higham - and the Guardian's head of audio Matt Wells.
The purpose of the attack, which began early on Thursday morning, is initially to draw people to the sites that hijack the accounts, and possibly install malware able to steal passwords on the user's computer. Another purpose may be simple identity theft: because people often use the same passwords and usernames on multiple services, getting access to one service can provide access to others too.
But in the longer term, the purpose may be to put the infected sites into search engine results.
The web security company F-Secure suggests that "We think it could have something to do with some of the recent search engine deals that have been made. Yahoo announced that they'll begin to include Twitter's real-time feed into their search results and Facebook is now included in Google's search results. The bad guys can use social networking trust to enhance their SEO [search engine optimisation] attacks."
Even results from hot topics may lead to scams and infected sites, F-Secure warns: "Always be careful when searching for hot topics. This "sea world trainer killed" example is currently being used in SEO attacks and many results will lead directly to scamware." It adds: "We expect to see fresh phishing attacks against Facebook before too long."
The attack spreads from each compromised account by sending out a "direct message" to people who follow the user, or simply putting the message in their Twitter feed. Anyone who then clicks on the links - whose destination is hidden by the use of a "URL shortener", which provides a shortened version of the link so that people are unaware of where the link actually takes them - is then at risk of having their account and machine taken over.
Twitter users are advised to follow Twitter safety account, which provides advice when such scams are spreading.
Twitter's status blog last night warned
"While simply receiving this message does not mean your account is compromised, if you do click through and enter your username and password, you'll want to change your password. If you've received this type of spam from a friend, you may want to alert them to change their password."
Such "phishing attacks" are increasingly common on both Twitter, where URL shortening - usually required to make standard URLs fit into the 140-character limit of the service - makes it harder to guard against dangerous links.
Account-shortening services such as bit.ly can block dangerous links, but only after they are alerted to them. The other option is to inspect the link before clicking on it - which the Twitter web page and Tweetdeck, a cross-platform program, do allow.
Spam and phishing attacks are a continual problem for Twitter, which is comparatively easy to join.
Charles Arthur
Friday 26 February 2010 11.10 GMT
guardian.co.uk © Guardian News and Media Limited 2010
An invitation to find out about better sex is spreading virally around Twitter – but only leads to identity theft and malware

Nick Higham of the BBC didn't send this message. And DO NOT follow the link.
Thousands of Twitter users have seen their accounts hijacked after a viral phishing attack which sends out messages saying "this you??" or "hey, i've been having better sex and longer with this here" and other sex-related "direct" messages.
Among those who fell victim were the Press Complaints Commission and the BBC correspondent Nick Higham - and the Guardian's head of audio Matt Wells.
The purpose of the attack, which began early on Thursday morning, is initially to draw people to the sites that hijack the accounts, and possibly install malware able to steal passwords on the user's computer. Another purpose may be simple identity theft: because people often use the same passwords and usernames on multiple services, getting access to one service can provide access to others too.
But in the longer term, the purpose may be to put the infected sites into search engine results.
The web security company F-Secure suggests that "We think it could have something to do with some of the recent search engine deals that have been made. Yahoo announced that they'll begin to include Twitter's real-time feed into their search results and Facebook is now included in Google's search results. The bad guys can use social networking trust to enhance their SEO [search engine optimisation] attacks."
Even results from hot topics may lead to scams and infected sites, F-Secure warns: "Always be careful when searching for hot topics. This "sea world trainer killed" example is currently being used in SEO attacks and many results will lead directly to scamware." It adds: "We expect to see fresh phishing attacks against Facebook before too long."
The attack spreads from each compromised account by sending out a "direct message" to people who follow the user, or simply putting the message in their Twitter feed. Anyone who then clicks on the links - whose destination is hidden by the use of a "URL shortener", which provides a shortened version of the link so that people are unaware of where the link actually takes them - is then at risk of having their account and machine taken over.
Twitter users are advised to follow Twitter safety account, which provides advice when such scams are spreading.
Twitter's status blog last night warned
"While simply receiving this message does not mean your account is compromised, if you do click through and enter your username and password, you'll want to change your password. If you've received this type of spam from a friend, you may want to alert them to change their password."
Such "phishing attacks" are increasingly common on both Twitter, where URL shortening - usually required to make standard URLs fit into the 140-character limit of the service - makes it harder to guard against dangerous links.
Account-shortening services such as bit.ly can block dangerous links, but only after they are alerted to them. The other option is to inspect the link before clicking on it - which the Twitter web page and Tweetdeck, a cross-platform program, do allow.
Spam and phishing attacks are a continual problem for Twitter, which is comparatively easy to join.
Charles Arthur
Friday 26 February 2010 11.10 GMT
guardian.co.uk © Guardian News and Media Limited 2010
