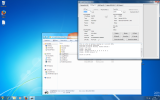
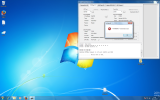
ok guys managed to get hold of a probe 3 and managed to dump the dvd key see below...does it look good ?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
JungleFlasher 0.1.95 Beta (321)
Session Started Wed Dec 02 20:34:21 2015
This is a Wow 64 process running on 4 x 64 bit CPUs
portio64.sys Driver Installed
portio64.sys Driver Started, thanks Schtrom !
Found 8 I/O Ports.
Found 1 Com Ports.
Found 7 windows drives C: D: E: F: G: H: I:
Found 2 CD/DVD drives D: E:
Drive is Lite-On..
Key found in KeyDB at record (1 - dump)
Key is: 141554E271CBFAC245C2ADCD3EF61966
Key has been tested and verified, thanks C4eva !
Drive is Lite-On..
Key found in KeyDB at record (1 - dump)
Key is: 141554E271CBFAC245C2ADCD3EF61966
Key has been tested and verified, thanks C4eva !
Sending Vendor Intro to port 0xEF00
Status 0x51
Re-sending Vendor Intro:
...................
Serial flash found with Status 0x52
Extracted drive key passed Verification !
key returned: 141554E271CBFAC245C2ADCD3EF61966
0000: 05 80 00 32 5B 00 00 00 - 50 4C 44 53 20 20 20 20 ...2[...PLDS
0010: 44 47 2D 31 36 44 32 53 - 20 20 20 20 20 20 20 20 DG-16D2S
0020: 30 32 35 31 30 43 41 30 - 41 30 44 36 30 38 43 47 02510CA0A0D608CG
0030: 37 33 38 38 30 38 30 30 - 33 34 38 20 20 20 00 00 73880800348 ..
0040: 00 00 00 00 00 00 00 00 - 00 00 00 00 00 00 00 00 ................
0050: 00 00 00 00 00 00 00 00 - 00 00 00 00 00 00 00 00 ................
0000: 05 80 00 32 5B 00 00 00 - 50 4C 44 53 20 20 20 20 ...2[...PLDS
0010: 44 47 2D 31 36 44 32 53 - 20 20 20 20 20 20 20 20 DG-16D2S
0020: 30 32 35 31 30 43 20 20 - 00 00 00 00 00 00 00 00 02510C ........
0030: 00 00 00 00 00 00 00 00 - 00 00 00 00 00 00 00 00 ................
0040: 00 00 00 00 00 00 00 00 - 00 00 00 00 00 00 00 00 ................
0050: 00 00 00 00 00 00 00 00 - 00 00 00 00 00 00 00 00 ................
0000: C0 85 00 00 00 00 00 00 - 00 00 00 00 00 00 00 00 ................
0010: 00 00 00 00 44 36 30 38 - 43 47 37 33 38 38 30 38 ....D608CG738808
0020: 30 30 33 34 38 20 20 20 - 00 00 00 00 00 00 32 30 00348 ......20
0030: 31 35 43 30 20 20 4C 50 - 53 44 20 20 20 20 47 44 15C0 LPSD GD
0040: 31 2D 44 36 53 32 20 20 - 20 20 20 20 20 20 20 20 1-D6S2
0050: 20 20 20 20 20 20 20 20 - 20 20 20 20 20 20 00 00 ..
0060: 00 00 00 0B 00 00 00 04 - 00 02 06 00 00 00 00 00 ................
0070: 00 00 00 00 00 00 00 00 - 00 00 00 00 00 00 00 00 ................
0080: 03 00 78 00 78 00 E3 00 - 78 00 00 00 00 00 00 00 ..x.x...x.......
0090: 00 00 00 00 00 00 00 00 - 02 02 00 00 68 00 00 00 ............h...
00A0: 00 00 00 00 00 00 00 00 - 00 00 00 00 00 00 00 00 ................
00B0: 20 20 00 00 ..
0000: 44 36 30 38 43 47 37 33 - 38 38 30 38 30 30 33 34 D608CG7388080034
0010: 38 20 20 20 FF FF FF FF - FF FF FF FF FF FF FF FF 8 ............
0020: FF FF FF FF FF FF FF FF - 41 30 FF FF FF FF FF FF ........A0......
0030: FF FF FF FF FF FF FF FF - FF FF FF FF FF FF FF FF ................
0040: FF FF FF FF FF FF FF FF - FF FF FF FF 41 30 FF FF ............A0..
Dummy.bin file saved to Dummy.bin
Loading firmware from buffer
Inquiry string found
Identify string found
Drive key @ 0xA030 141554E271CBFAC245C2ADCD3EF61966
Firmware Osig: [PLDS DG-16D2S 0251]
Firmware is: PhatKey Extract
Key database updated