You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Nagra Hex block Decryption
- Thread starter fes_786
- Start date
- Status
- Not open for further replies.
Khalil Bouayad
Member
- Joined
- Mar 4, 2017
- Messages
- 17
- Reaction score
- 8
Can you upload in megapictures
Benfica200
DW Member ++
- Joined
- Dec 1, 2013
- Messages
- 280
- Reaction score
- 219
Dont know why you need BK and RSA!pictures
This card work only in cak7.. the keys are public!
electron112
DW Member +
i have some problem to find rawdata in my dump if one help please
Khalil Bouayad
Member
- Joined
- Mar 4, 2017
- Messages
- 17
- Reaction score
- 8
get rodata using binwalk in nand flash or stlinux in .rodata or in SH40 in the flash nor in cak7
electron112
DW Member +
thanks
terrestrial
Inactive User
- Joined
- Feb 15, 2017
- Messages
- 44
- Reaction score
- 11
This picture is fake! dognaldo.
If they don't even know the difference between eCWs, dCWs eCWPK and dCWPKs as you can clearly see in the picture (CWPK00 and the dCW are the same) How the hell can you expect this to be true? And bruteforce takes years, It's not as easy as running a simple brute_des.exe tool. Forget It.
If they don't even know the difference between eCWs, dCWs eCWPK and dCWPKs as you can clearly see in the picture (CWPK00 and the dCW are the same) How the hell can you expect this to be true? And bruteforce takes years, It's not as easy as running a simple brute_des.exe tool. Forget It.
This picture is fake! dognaldo.
If they don't even know the difference between eCWs, dCWs eCWPK and dCWPKs as you can clearly see in the picture (CWPK00 and the dCW are the same) How the hell can you expect this to be true? And bruteforce takes years, It's not as easy as running a simple brute_des.exe tool. Forget It.
Maybe yes maybe no. And found key´s, fake too ? Did you test ?
Be a good observer. We have 4 bytes of the key ! What makes the process so much easier !
Stay with your truths and be happy.
Like I said, just for fun.
Last edited:
terrestrial
Inactive User
- Joined
- Feb 15, 2017
- Messages
- 44
- Reaction score
- 11
Maybe yes maybe no. Maybe i´m fake too.
Be a good observer. We have 4 bytes of the key ! What makes the process so much easier !
Stay with your truths and be happy.
Like I said, just for fun.
Actually you have 8 bytes (the key is 16) and you need the other 8, which still takes a very long time to bruteforce. And under normal circumstances you wouldn't have any bytes. The picture is also a photoshop because the initial key is only 8 bytes long... someone edited out the rest of the key... but even then this is worth nothing if you don't have the corresponding NUID.
If you have that brute_3des tool send us a link, but i'm guessing you don't either.
Actually you have 8 bytes (the key is 16) and you need the other 8, which still takes a very long time to bruteforce. And under normal circumstances you wouldn't have any bytes. The picture is also a photoshop because the initial key is only 8 bytes long... someone edited out the rest of the key... but even then this is worth nothing if you don't have the corresponding NUID.
If you have that brute_3des tool send us a link, but i'm guessing you don't either.
Again, try to be a good observer!
Look at the differences between des and 3des. Understand why 4 bytes.
If it were 8 bytes I would not waste time trying.
This is only the first step, NUID will only be used in the last step.
--> vvv.sat-universe.com/showthread.php?t=301544&page=6
Tdes:. SYSID 3411 = 6F XX 27 XX 9B XX 86 XX 6F XX 27 XX 9B XX 86 XX
(by onsitbin #748)
3Des_ecb decrypt
(Data = 16bytes, Key=16bytes (k1=k3))
data encrypt = BF 3F 84 D1 50 CA A3 99 09 AD F4 13 7B C7 5B 58
3Des decrypt Key = 6F 0E 27 3A 9B BC 86 F6 6F 0E 27 3A 9B BC 86 F6
data decrypt = 2A C9 F5 6A 35 B5 18 6D E5 E5 93 B0 BD B0 DA F2
Try with these 16 bytes (8 + 8) key´s too;
6F0E273A9BBC86F76F0E273A9BBC86F7
6F0E273A9BBD86F66F0E273A9BBD86F6
6F0E273A9BBD86F76F0E273A9BBD86F7
6F0E273B9BBC86F66F0E273B9BBC86F6
6F0E273B9BBC86F76F0E273B9BBC86F7
6F0E273B9BBD86F66F0E273B9BBD86F6
6F0E273B9BBD86F76F0E273B9BBD86F7
Des_ecb decrypt
(Data = 8bytes, Key=8bytes = k1)
data encrypt = BF 3F 84 D1 50 CA A3 99
Des decrypt Key = 6F 0E 27 3A 9B BC 86 F6
data decrypt = 2A C9 F5 6A 35 B5 18 6D
Try with these 8 bytes key´s too;
6F0E273A9BBC86F7
6F0E273A9BBD86F6
6F0E273A9BBD86F7
6F0E273B9BBC86F6
6F0E273B9BBC86F7
6F0E273B9BBD86F6
6F0E273B9BBD86F7
correct key ? Who knows !!!
[ ] ´s
terrestrial
Inactive User
- Joined
- Feb 15, 2017
- Messages
- 44
- Reaction score
- 11
Again, try to be a good observer!
Look at the differences between des and 3des. Understand why 4 bytes.
If it were 8 bytes I would not waste time trying.
This is only the first step, NUID will only be used in the last step.
--> vvv.sat-universe.com/showthread.php?t=301544&page=6
Tdes:. SYSID 3411 = 6F XX 27 XX 9B XX 86 XX 6F XX 27 XX 9B XX 86 XX
(by onsitbin #748)
3Des_ecb decrypt
(Data = 16bytes, Key=16bytes (k1=k3))
data encrypt = BF 3F 84 D1 50 CA A3 99 09 AD F4 13 7B C7 5B 58
3Des decrypt Key = 6F 0E 27 3A 9B BC 86 F6 6F 0E 27 3A 9B BC 86 F6
data decrypt = 2A C9 F5 6A 35 B5 18 6D E5 E5 93 B0 BD B0 DA F2
Try with these 16 bytes (8 + 8) key´s too;
6F0E273A9BBC86F76F0E273A9BBC86F7
6F0E273A9BBD86F66F0E273A9BBD86F6
6F0E273A9BBD86F76F0E273A9BBD86F7
6F0E273B9BBC86F66F0E273B9BBC86F6
6F0E273B9BBC86F76F0E273B9BBC86F7
6F0E273B9BBD86F66F0E273B9BBD86F6
6F0E273B9BBD86F76F0E273B9BBD86F7
Des_ecb decrypt
(Data = 8bytes, Key=8bytes = k1)
data encrypt = BF 3F 84 D1 50 CA A3 99
Des decrypt Key = 6F 0E 27 3A 9B BC 86 F6
data decrypt = 2A C9 F5 6A 35 B5 18 6D
Try with these 8 bytes key´s too;
6F0E273A9BBC86F7
6F0E273A9BBD86F6
6F0E273A9BBD86F7
6F0E273B9BBC86F6
6F0E273B9BBC86F7
6F0E273B9BBD86F6
6F0E273B9BBD86F7
correct key ? Who knows !!!
[ ] ´s
Actually I know... it's not the correct key and the calculation is WRONG!
The 3des decrypt keys are 16 bytes and never 8 bytes repeating itself, that's not the way the keyladder works. Why use a mechanism which has 3 stages and then use a constant key on stage 2 ?? That would defeat the entire purpose, wouldn't it? The calculation makes no sense and does not work for HD+ either or any keys from a HD+ box. The only key which resembles two times the same 8 bytes is the nano 01 key (kS1k1mod1 XOR kS11k1mod2 from ROdata) and it's not used this way.
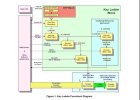
I suggest you look at the keyladder mechanism again. (see pic.... k1 is the dcwpk ;-) Also the NUID is involved from the TOP of the keyladder and not in the last step!
No offence dude... but really i have seen no proof this is real data, just some made up numbers. And onsitbin maybe knows alot but he's not gonna share it. The only thing you are doing is putting people on the wrong track.
If you think this is real..... post the corresponding NUID so we can see if it works with our HD+ cards.
Actually I know... it's not the correct key ..............
Let's try it another way.
First, a suggestion regarding the correct understanding of block 97.
See this --> vvv.dragteam.info/threads/n3-bloco-hex.187670/page-3#post-916540
Read all calhordas member" post´s, it's a good read.
[ ]´s
electron112
DW Member +
im member this forum but no access for this post

Benfica200
DW Member ++
- Joined
- Dec 1, 2013
- Messages
- 280
- Reaction score
- 219
just bullshit, it was good if it was that simple.
electron112
DW Member +
if can me explain i have problem with cmd 03 instruction sending by box to card
and the card reply with wrong aes and cant have session key
and the card reply with wrong aes and cant have session key
bbzzyyczczeek
Inactive User
- Joined
- Nov 17, 2013
- Messages
- 22
- Reaction score
- 0
How calculate gen MOD1, MOD2, DATA88?
Eny help
Eny help
jesuchrist
Member
- Joined
- Aug 29, 2013
- Messages
- 21
- Reaction score
- 1
see the post #729
bbzzyyczczeek
Inactive User
- Joined
- Nov 17, 2013
- Messages
- 22
- Reaction score
- 0
ok.
- Status
- Not open for further replies.
Similar threads
- Replies
- 0
- Views
- 5K
- Replies
- 3
- Views
- 4K